Why Purchase Price Is No Longer Enough In an era of constant budget optimization, technology investm...
.png)
.png)
Why Purchase Price Is No Longer Enough In an era of constant budget optimization, technology investm...

The discovery of CVE-2025-5777, dubbed CitrixBleed 2, highlights the systemic flaws inherent in trad...

In a world of evolving threats, these five tactics form the core of practical cybersecurity in 2025.

I. Browsing the web is like navigating a sea of threats Browsers are crucial for digital tasks, but ...

Security, scalability, trust. In a rapidly changing, remote, hyper-collaborative Media & Entertainme...

Google Meet, Webex, Microsoft Teams, Zoom. These names have become the soundtrack of our professiona...

Nowadays, companies juggle a growing volume of data daily. Whether it's customers' personal informat...

How to Define SASE and ZTNA The rise of remote work, the increasing adoption of cloud services, and ...

As the remote work landscape continues to evolve, businesses are seeking secure, high-performance al...
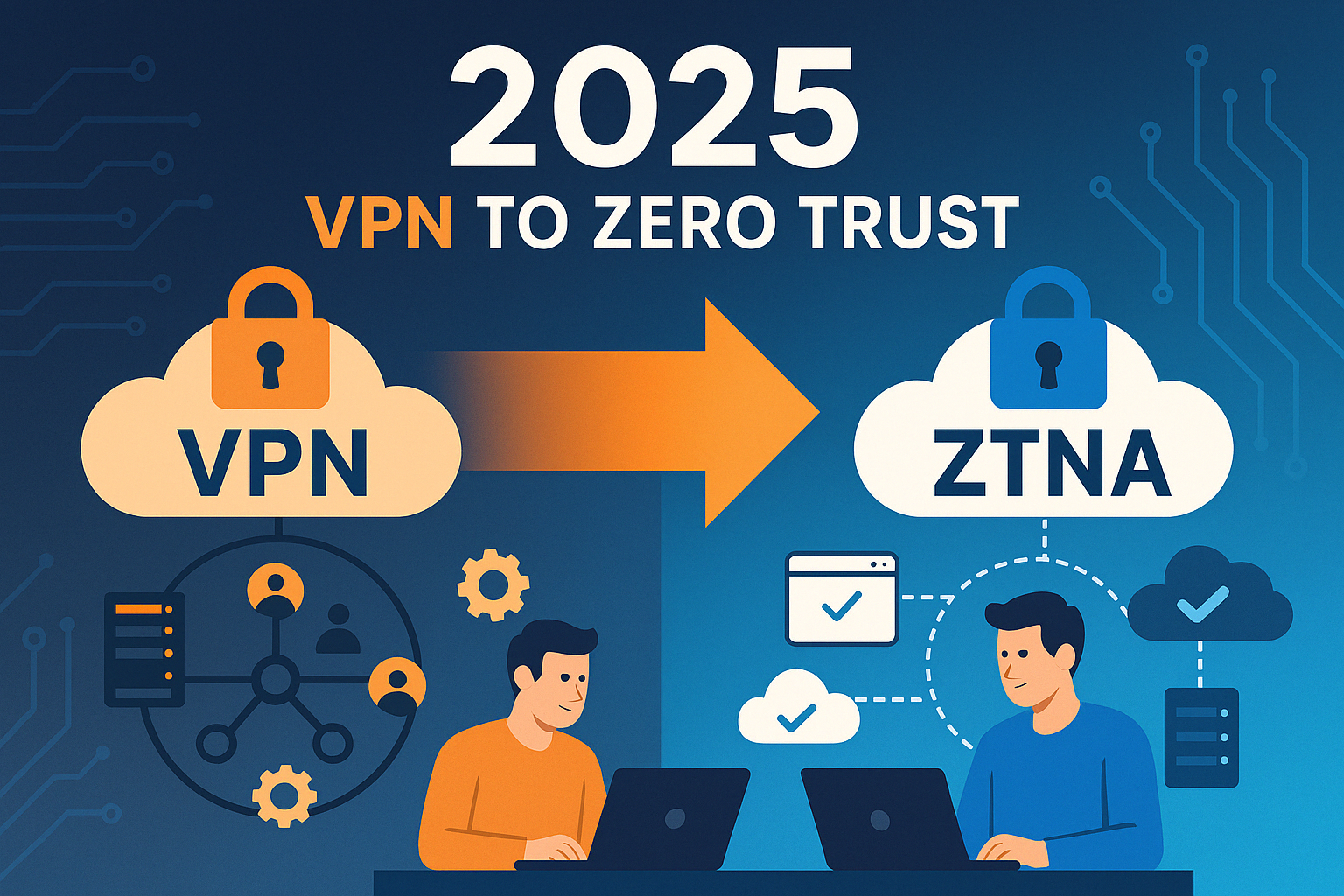
Enterprise network architecture is changing radically in the age of the cloud and hybrid working. Ma...

At Reemo, we don’t just provide remote access.
We help you regain full control over your remote work environments — securely and efficiently.
✔ An intuitive interface built for IT efficiency
✔ A zero-trust architecture to protect your critical assets
✔ Business-focused features: fine-grained access control, real-time supervision, built-in auditability
✔ And a fast deployment, with no infrastructure to maintain
🧮 Talk to an expert at Reemo with Reemo and see how you can secure your company's remote access without compromising on performance.
Discover our conversations with industry professionals about their work